As Kubernetes remains the bedrock of container orchestration, it is increasingly crucial for DevOps experts to fully grasp its configurations and functionalities. In 2024, specific Kubernetes configurations are particularly noteworthy for their capacity to amplify automation, security, and performance within cloud-native environments. This article extensively explores 13 indispensable Kubernetes configurations, providing in-depth analysis for each, including practical use cases, advantages, and illustrative code samples.
➠Resource Allocation: Requests and Limits Mastering the precise setup of resource requests and limits is fundamental within Kubernetes. This practice guarantees that your applications are adequately equipped with resources for optimal performance, while also preventing any single application from excessively monopolizing cluster resources.
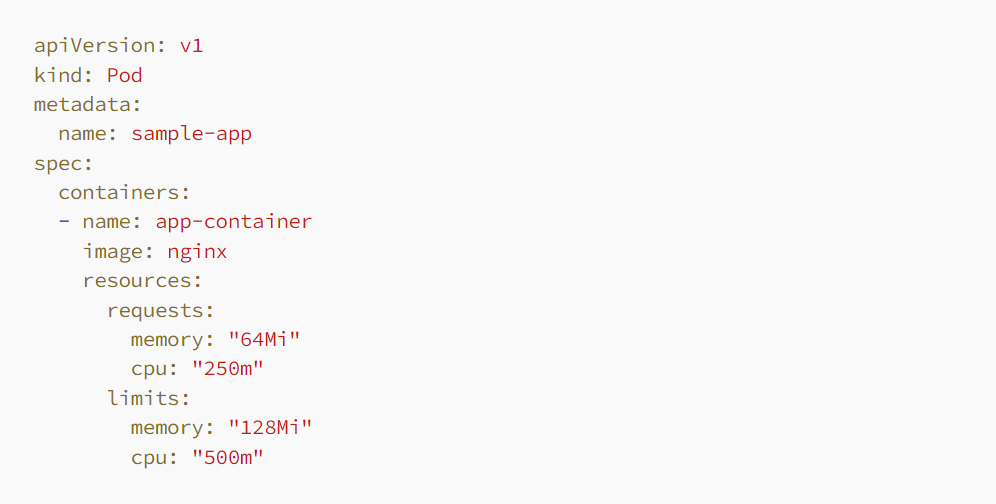
- Purpose: This configuration is essential for upholding the stability and efficiency of both individual applications and the entire cluster. It mitigates resource conflicts and safeguards against unexpected termination of applications resulting from resource scarcities.
- Relevant Audience: Crucial for Kubernetes administrators and developers striving to enhance application performance and maximize cluster resource utilization.
- Appropriate Timing: Implement this configuration for every workload to ensure consistent application performance and to mitigate the risk of any single application excessively consuming resources, thereby safeguarding cluster stability.
➠Management of Liveness and Readiness: Liveness and readiness probes play a pivotal role in overseeing the lifecycle of applications within Kubernetes. They enable Kubernetes to make informed decisions regarding container restarts (liveness) and readiness to accept traffic (readiness).
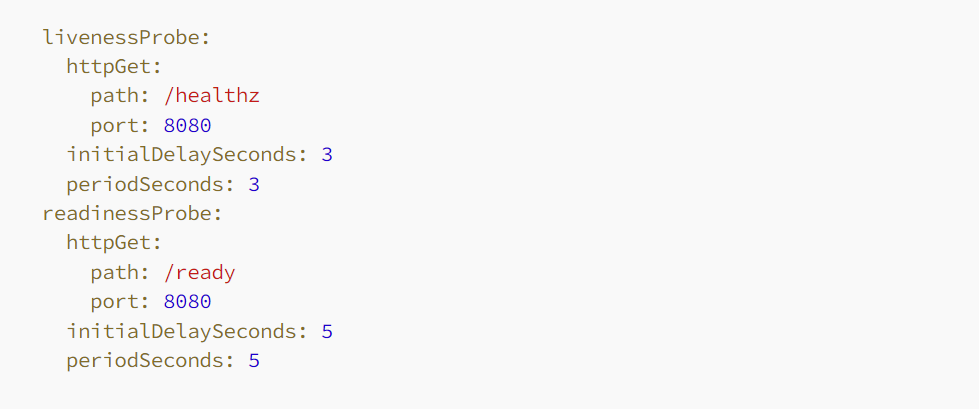
- Importance: These probes bolster the resilience and accessibility of your applications by empowering Kubernetes to autonomously manage container states based on actual application health rather than mere container runtime status.
- Target Audience: Developers and operators deploying essential services necessitating high availability and self-recovery capabilities.
- Appropriate Usage: Integrate liveness probes for applications where uninterrupted operation is paramount, and readiness probes for applications requiring readiness before serving requests.
➠Externalization of Configuration and Sensitive Data. ConfigMaps and Secrets play an essential role in separating configuration settings and sensitive data from application code. ConfigMaps store non-confidential data in key-value pairs, whereas Secrets are designed for handling sensitive information.
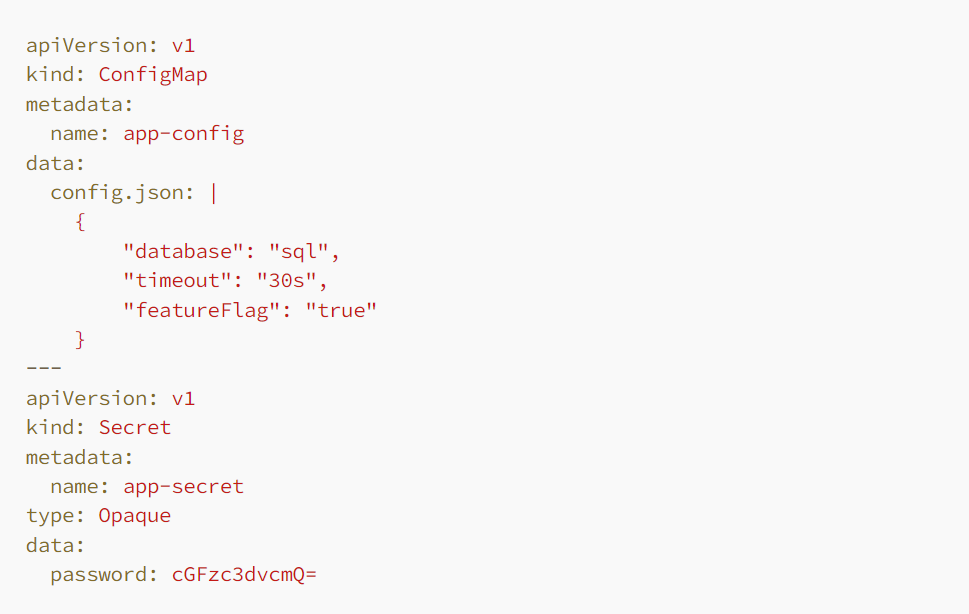
- Importance: These configurations detach configuration and secrets from application logic, streamlining application deployment and management across diverse environments while bolstering security measures.
- Target Audience: Crucial for all Kubernetes users managing applications that necessitate configuration data or require secure handling of credentials and other sensitive information.
- Appropriate Usage: Utilize ConfigMaps for application configuration that varies across environments (such as development, staging, production), and employ Secrets for managing credentials, tokens, or any other sensitive data.
➠ Horizontal Pod Autoscaler (HPA). The Horizontal Pod Autoscaler dynamically regulates the quantity of pod replicas within a Deployment, ReplicaSet, or StatefulSet, depending on observed CPU utilization or custom metrics.
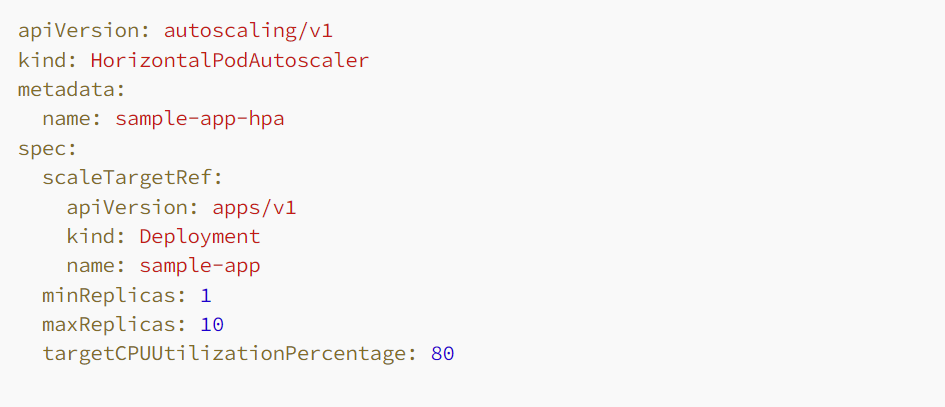
- Significance: HPA guarantees that your application scales out to accommodate increased demand and scales in during periods of decreased demand, thereby optimizing resource utilization and preserving performance.
- Target Audience: Administrators and DevOps experts seeking to automate application scaling in response to fluctuating demand.
- Appropriate Timing: Suited for applications experiencing variable traffic, ensuring seamless allocation of resources to match demand without requiring manual adjustments.
➠ Implementation of Network Policies. Network policies serve as Kubernetes resources governing traffic flow between pods and network endpoints, facilitating microsegmentation and bolstering the security of Kubernetes applications.
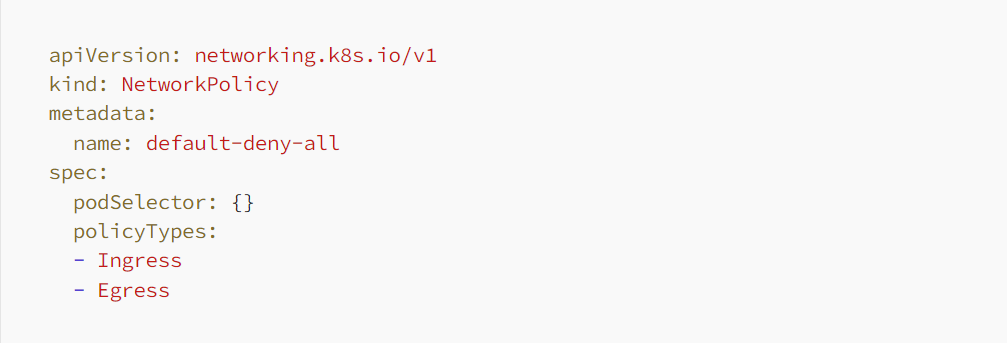
- Importance: These policies are vital for safeguarding pod communications within Kubernetes clusters, allowing only authorized traffic to traverse between pods or external services.
- Target Audience: Kubernetes administrators and security-minded engineers tasked with enforcing stringent network security policies within their clusters.
- Appropriate Usage: Particularly beneficial in multi-tenant environments or applications demanding high security standards, aiming to thwart unauthorized access and mitigate potential attack avenues.
These advanced Kubernetes configurations lay the groundwork for developing resilient, streamlined, and secure cloud-native applications. Proficiently grasping and utilizing these configurations empowers engineers to harness Kubernetes’ capabilities fully, customize deployments according to specific requirements, and uphold superior operational standards.
Complete the form located at this page https://synpass.pro/contactsynpass/ in order to get in touch with us regarding your project☝

